Imagine this: You’re working on your computer and you observe that it gets slower. Or maybe you are unable to access text or media files that were earlier available.
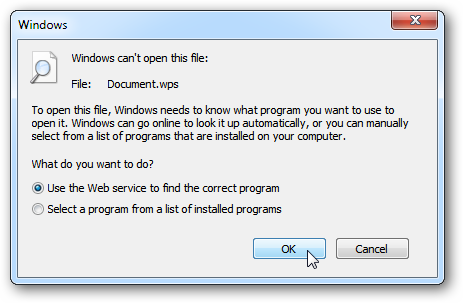
Windows might be sending you error messages notifying that a file is of an “Unknown file type” or “Windows can’t open this file.”
Another likelihood is that you’re totally locked out of your system. If you’re at work, you might be noticing that other people are facing the same issue. Some are already locked out, and others are still unsure about what’s happening, just as you are.
Then you come across a message testifying to your fears.
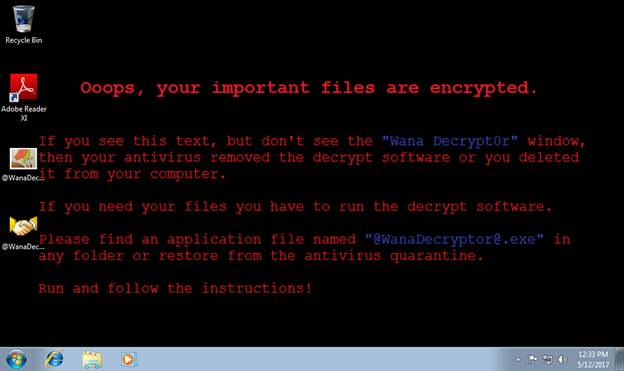
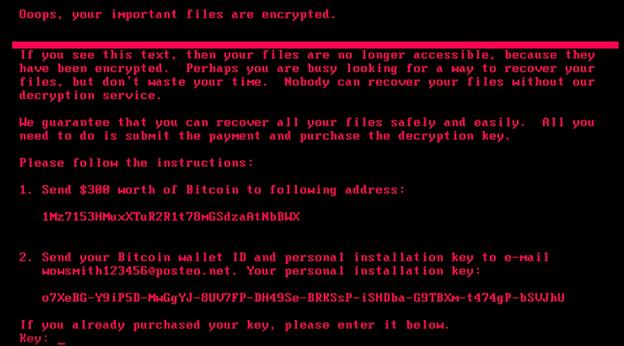
You’ve been attacked by ransomware.
How Does Ransomware Work?
Ransomware generally spreads through junk or phishing emails, as well as websites or drive-by downloads. Infection methods are continually developing and there are several other ways one can become infected. Encrypting ransomware is so far the most common recent variety of ransomware. Other types that might be encountered are:
• Non-encrypting ransomware or lock screens
• Ransomware that encodes the Master Boot Record (MBR) of a drive or Microsoft’s NTFS
• Leakware or extortionware
• Mobile Device Ransomware
Wrong sense of security ruse
All kinds of system security threats, including ransomware, are fundamentally one or a blend of various motivators. When someone attacks your system, they are typically trying to steal something worthwhile from your company or from your people. Or, they’re trying to stop you from accessing systems that are important to you so that you’ll pay a sum of money to regain that access.
With their security technologies in place, a number of organizations are tricked into a wrong sense of safety about ransomware thinking they’re fully protected with antivirus measures. They, however, fail to realize how a ransomware attack can infiltrate even the most ostensibly well-prepared defenses. With ransomware, there are several points of entry, and only one has to work for the attacker.
Backup systems are also vulnerable
Contrary to the general belief, backup systems are also vulnerable. When SamSam ransomware in 2018 attacked a VectorUSA client, the client lost a whopping 200 servers and all their backups within just half an hour. Also, ransomware attacks in 2019 have risen rapidly with more than 70 attacks reported in the first half of the year.
Recent ransomware attacks have also hit many organizations, rekindling a subject that once was the burning issue in the early 2000s.
While there is no single tried-and-tested ransomware attack solution, or technology to prevent ransomware attacks, there are proactive measures one can take to avoid them. In addition to basic blocking and tackling, it’s important to reduce your “attack surface.” Next, there’s a need to segment your IT systems because when a ransomware attack does take place, you can easily separate the damage and recover swiftly. Finally, your backup systems have to be impervious to the attack and be available to recover as soon as possible.
Ransomware is becoming more complex
One of the most worrying features of the threat from ransomware is that it has grown increasingly complex over the last few years. Hacking has progressed into creating sophisticated companies that offer help desks, toll-free phone numbers and more. Worryingly, it all works very well. And don’t think that only large enterprises are the only target of these organizations—small companies generating less than a million dollars a year are equally susceptible. And attacks on them can be very beleaguered by a very gifted attacker. For example, if a hacker living in a place where $5 an hour is a common wage spends a whole day targeting an organization in order to acquire a $10,000 payment, their potential payoff is enormous.
Undoubtedly, it will be hugely difficult to recover from a ransomware attack if you’re not suitably prepared. You’re fundamentally restricted to two things:
1. Recognize the source of the attack and ensure that the attack is prevented.
2. Recognize the important systems that will put you back in business or your organization back in operation, and what you need to do to recover.
But what may first seem as the most noticeable systems required to be operational may truly be different than you might expect. For example, in school districts, many leaders recognize payroll and student information systems as the most serious to keep their schools open. Nevertheless, from an operational position, that’s not inevitably the case.
Apart from a ransomware attack, if the school district were to suffer some kind of catastrophe or other troublesome event, many school districts can keep open without their payroll or student information system for an amazingly long time. What the district couldn’t instantly operate without are transportation and food services, not to mention plumbing.
When you prudently inspect IT systems that support overall operations, one need not be emotional before and after a ransomware attack. The main top-level worries when in recovery are to determine what’s been lost while recognizing the swiftest way to keep schools open. The bare minimum system requirements will also be needed to restart operations and a recovery plan to restore those systems. The plan for preventing another attack. If you decide to pay the attacker’s ransom, another ransomware attack may quickly follow your recovery.
Prepare now to fully recover later
You should consider yourself lucky if you have never been a victim of ransomware. But you still err on the side of caution. Instead of waiting for an attack to take place, you should be fully prepared to thwart such attacks. And in case you’ve not been able to prevent these attacks, you should be prepared to recover from them once they strike you.
Speaking with someone who’s actually worked with businesses and enterprises that have suffered ransomware attacks, and who comprehends how attackers think, will provide you a better viewpoint on what you need to protect yourself. By setting up elementary security technologies and sound management procedures now that will restrict your ransomware exposure, you’ll be much better equipped to stay in business or operation if you become a victim of a ransomware attack.
Tips on how to recover from ransomware
Establishing preemptive measures is not always completely effective. These few tips will help you recover from a ransomware attack as effectively as possible.
• Find out what kind of ransomware is attacking you – Recognizing the ransomware you’ve had to deal with will help ascertain what retrieval options one has. The best way to do this is to establish how much of your data you can still access.
• Detach from everything – The most significant thing one can do is to limit the effect of the ransomware infection by detaching your device to stop the virus from spreading throughout the network.
• Take a picture of the ransomware screen – When attacked, there will be a note showing that identifies the ransom, including the amount to be paid and where to send the payment. Taking a picture so the information is easily available for when the suitable authorities are contacted can be quite helpful.
• Follow appropriate measures to counter the attack – If you have been attacked, come up with the incident response policy instantly because this is a security breach. Follow the steps delineated in your policy to make sure that all of the right steps are taken, including informing stakeholders of the breach.
• Research the ransomware –Depending on the type of ransomware that’s attacked you, data recovery may be possible using software available online. It is also likely that there is a way to decipher the encoded files without having to pay the ransom. If you don’t have the internal resources to identify the type of ransomware that’s infected you, get in touch with a reliable cybersecurity company for help.
• Try restoration from backups – You may, if possible, want to retrieve your systems from any backups on hand. Nevertheless, be aware that since the ransomware may have been in your system for some time, any backups could be affected as well. Before restoring, ensure to arrange an antivirus software through your system.
Types of ransomware
Ransomware is of two types: crypto ransomware and locker ransomware.
Crypto ransomware encodes important files on a computer, discouraging the user to access them. Attackers that launch crypto ransomware attacks earn heavily by getting the victims to pay a ransom to get their files back.
Locker ransomware does not encode files. Instead, it locks the victim out of their device, stopping them from using it.